In todays task we’re going to research and investigate mitigation and proactive security.
Learning Objectives #
- Learn to understand incident analysis through the Diamond Model.
- Identify defensive strategies that can be applied to the Diamond Model.
- Learn to set up firewall rules and a honeypot as defensive strategies.
Overview #
This is my key takeaways from today:
- Intrusion detection and prevention is a critical component of cyber security aimed at identifying and mitigating threats.
Incident Analysis #
In reason tasks we have identified clues and artefacts, but yet to piece them together to lead us to the attacker. We need a framework to profile the attacker, understand their moves and help us strengthen our defences.
The Diamond Model is a security framework that seasoned professionals use to unravel the mysteries of adversary operations (and identify the elements used in an intrusion). It has four core facets:
- Adversary
- Victim
- Infrastructure
- Capability
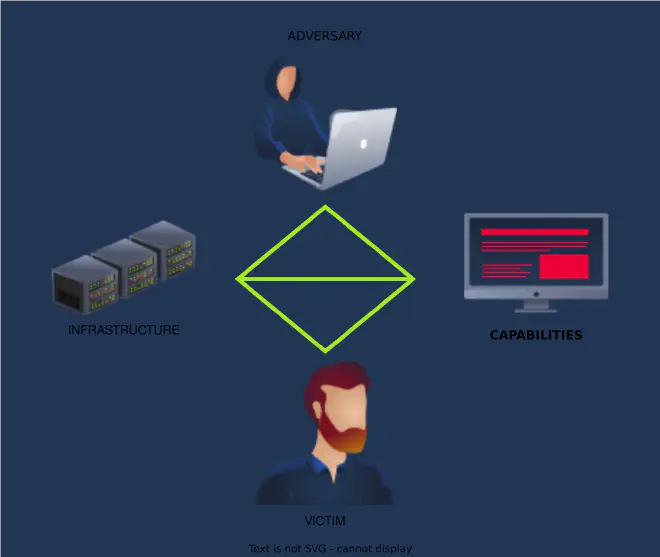
Adversary #
Adversary operators can be an individual or an entire organisation aiming to disrupt the operations of another. There’s also Adversary customers. They are the one who reaps the rewards from the cyberattack and can consolidate the efforts of various adversary operators.
Victim #
It can be a single individual, domain or entire organisation with multiple networks and data assets.
Infrastructure #
Every adversary needs tools. They require software/hardware to execute their malicious objectives. Infrastructure is the physical and logical interconnections that an adversary employs. Can be owned and controlled by adversaries or even intermediaries like service providers.
Capability #
This is where we shine a light on tactics, techniques and procedures (TTPs) that shape adversaries endeavours. Some examples include:
- Phishing: Adversaries may use deceptive emails or messages to trick individuals into revealing sensitive information or clicking on malicious links.
- Exploiting vulnerabilities: Adversaries can exploit weaknesses or vulnerabilities in software, systems, or networks to gain unauthorised access or perform malicious actions. This was very well showcased on AOC Day 10, where we covered SQL injection as one of the techniques used.
- Social engineering: This involves manipulating individuals through psychological tactics to gain unauthorised access or obtain confidential information.
- Malware attacks: Adversaries may deploy malicious software, such as viruses, worms, or ransomware, to gain control over systems or steal data.
- Insider threat: This refers to individuals within an organisation who misuse their access privileges to compromise systems, steal data, or disrupt operations.
- Denial–of–service (DoS) Attacks: Adversaries may overwhelm a target system or network with excessive traffic or requests, causing it to become unresponsive or crash.
Defensive Capability #
Two key elements of defensive capability are threat hunting and vulnerability management.
Threat hunting is a proactive and iterative process to actively search for signs of malicious activities or security weaknesses within the organisation’s network and systems. Threat hunters analyse behavioural patterns, identify advanced threats and improve incident response.
Vulnerability management is a structured process of identifying, assessing, prioritising, mitigating and monitoring vulnerabilities in an organisation’s systems and applications.
Firewall #
Santa’s elves building a wall as McSkidy overlooks with disgust.The mighty firewall is a guardian of networks and a sentinel of cyber security! This network security device stands vigilant, monitoring and controlling the ebb and flow of incoming and outgoing network traffic. With its predetermined security rules, a firewall can repel a wide range of threats, from unauthorised access to malicious traffic and even attempts to breach sensitive data.
Firewalls come in many forms, including hardware, software, or a combination. Their presence is vital, a cornerstone of any cyber security defence strategy. The following are the common types of firewalls that exist:
- Stateless/packet-filtering: This firewall provides the most straightforward functionality by inspecting and filtering individual network packets based on a set of rules that would point to a source or destination IP address, ports and protocols. The firewall doesn’t consider any context of each connection when making decisions and effectively blocks denial–of–service attacks and port scans.
- Stateful inspection: This firewall is more sophisticated. It is used to track the state of network connections and use this information to make filtering decisions. For example, if a packet being channelled to the network is part of an established connection, the stateful firewall will let it pass through. However, the packet will be blocked if it is not part of an established connection.
- Proxy service: This firewall protects the network by filtering messages at the application layer, providing deep packet inspection and more granular control over traffic content. The firewall can block access to certain websites or block the transmission of specific types of files.
- Web application firewall (WAF): This firewall is designed to protect web applications. WAFs block common web attacks such as SQL injection, cross-site scripting, and denial-of-service attacks.
- Next-generation firewall: This firewall combines the functionalities of the stateless, stateful, and proxy firewalls with features such as intrusion detection and prevention and content filtering.
Honeypot #
A honeypot is a cyber security mechanism - a masterful deception. It presents itself as an alluring target to the adversaries, drawing them away from the true prizes. They come in various forms: Software applications, servers or entire networks. They are designed to mimic legitimate targets, but are under the watchful control of the defender.
Honeypots can be classified into two main types:
- Low–interaction honeypots: These honeypots artfully mimic simple systems like web servers or databases. They gather intelligence on attacker behaviour and detect new attack techniques.
- High–interaction honeypots: These honeypots take deception to new heights, emulating complex systems like operating systems and networks. They collect meticulous details on attacker behaviour and study their techniques to exploit vulnerabilities.
Honepot demonstration #
We’re going to setup a honeypot called PenTBox.
Questions #
- Which security model is being used to analyse the breach and defence strategies?
The entire task is based about this model.
- Which defence capability is used to actively search for signs of malicious activity?
Answer found under Defensive Capability.
- What are our main two infrastructure focuses? (Answer format: answer1 and answer2)
The entire task is centered around these two tasks. You have tested the two if you followed along in the task on tryhackme.
- Which firewall command is used to block traffic?
You use ALLOW to allow network traffic, and **** to block the traffic…
- There is a flag in one of the stories. Can you find it?
This one was a little trickier.
Run the script on the box (Van_Twinkle_rules.sh). It sets up the firewall rules for you.
Then run sudo ufw status verbose to see the current rules.
Open up the port 8090 and visit the website.
The website was quite big so I just curl -s http://<IP>:8090 | grep -i thm{ to find the flag..
